A Browser Helper Object or BHO is a DLL module designed as an add-on for Microsoft’s Internet Explorer web browser to provide added functionality. When a BHO is installed on your system the add-on loads up automatically every time Internet Explorer is started. Hackers have been abusing this functionality by installing malicious BHOs stealing user’s online banking passwords and carrying out all sorts of other malicious activities.
While analysing a particular malware “convite.exe” which is detected by McAfee as “PWS-Banker!dtl” I noticed something quite interesting and therefore decided to post my findings. Among the various files being dropped by the malware one file was of particular interest called “flashcpx.dll” which gets installed as a BHO.
When a BHO gets registered onto the system it adds various keys in the registry. When Internet Explorer starts up it reads the registry location below telling Internet Explorer which BHOs it needs to load up. Let’s look at an example of Adobe’s BHO installed on my machine “AcroIEHelperShim.dll”.
[HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects]
{18DF081C-E8AD-4283-A596-FA578C2EBDC3}
In this key location lists 16-byte CLSID strings for the BHOs. Using this string it then points to another location in the registry telling Internet Explorer which DLL module to load up.
[HKLM\SOFTWARE\Classes\CLSID\{18DF081C-E8AD-4283-A596-FA578C2EBDC3}\InprocServer32]
C:\Program Files\Common Files\Adobe\Acrobat\ActiveX\AcroIEHelperShim.dll
Now when the malicious “flashcpx.dll” BHO gets installed it does something clever to hide its presence yet still manage to load up. As you can see below the CLSID string is longer than usual. The added characters cause most tools not to list out the BHO even though Internet Explorer loads it up.
[HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects]
{399BFACE-3ADA-4DAE-80D8-E221812243A9}80D8-E221812243A9}
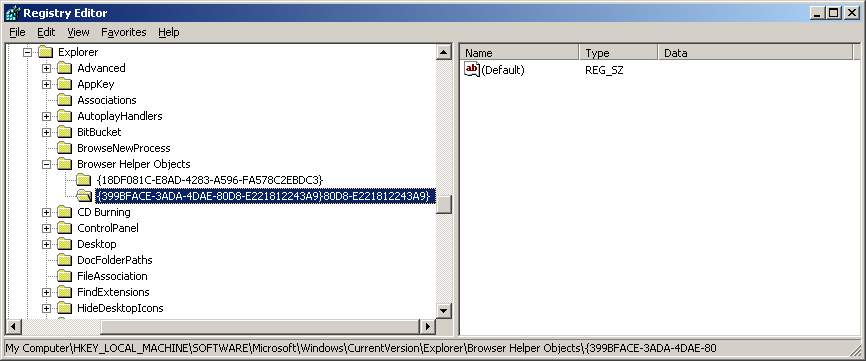
When Internet Explorer loads up the BHO the browser only reads 16-byte CLSID format {399BFACE-3ADA-4DAE-80D8-E221812243A9} and then loads up the BHO via the normal process. So any added characters are ignored by Internet Explorer.
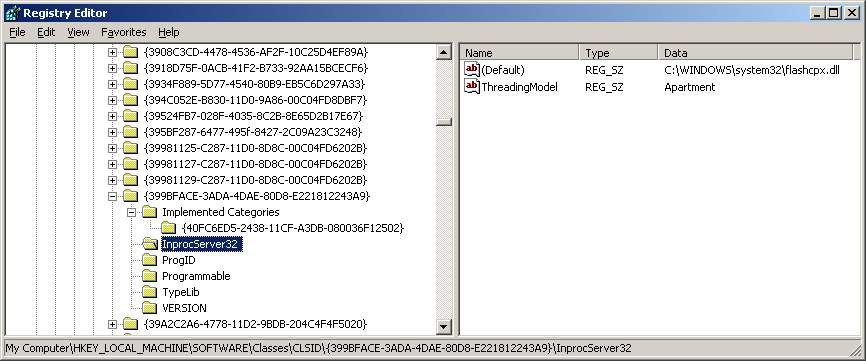
[HKLM\SOFTWARE\Classes\CLSID\{399BFACE-3ADA-4DAE-80D8-E221812243A9}\InprocServer32]
C:\WINDOWS\system32\flashcpx.dll
For example, if we wanted to see what BHO are installed we can use Internet Explorer’s Manage Add-ons or use SysInternals Autoruns.exe. Both do not show the malicious BHO installed as these tools reads the entire string instead of the 16-byte CLSID format which Internet Explorer does do.
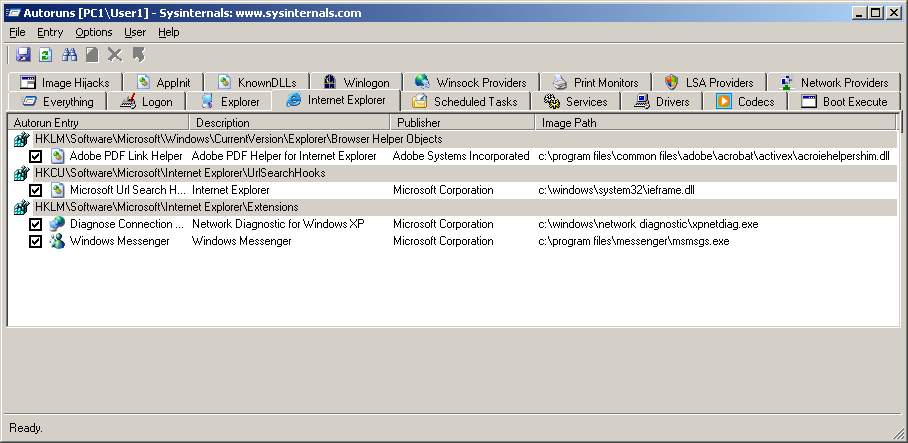
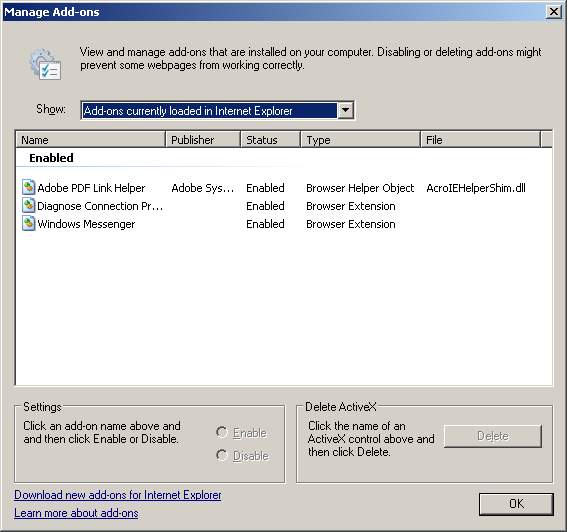
Since the string is longer than recommended when it goes to find the CLSID key in [HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID] the key is not found and therefore the DLL module does not get listed. Quite odd that “manage add-ons” is part of Internet Explorer but does not list it yet happy to load up the BHO :).
Reference:
http://www.threatexpert.com/report.aspx?md5=3765371819c1195f3cdbb255f4442e1e