Another fake antivirus software calling itself “XP Guardian 2010” is doing its rounds displaying bogus pop-ups and fake scans enticing you to buy its product. What is interesting about this malware is that this one changes the machine exe associations in the Windows registry. When any executable with an exe extension is manually or automatically run this malware is loaded first which then calls the original executable.
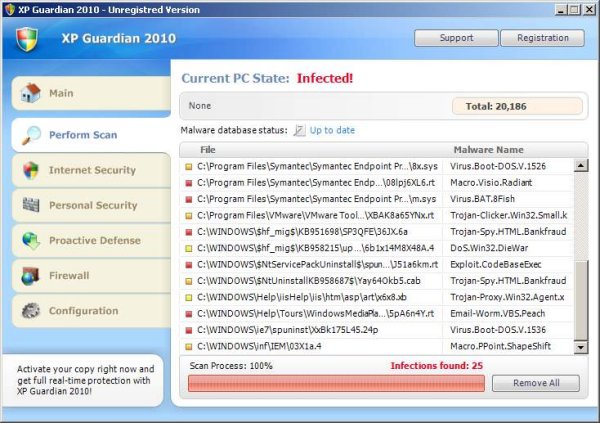
When an executable is first run it checks various entries in the registry before loading the program. Once a machine has been infected by this malware the call is hijacked to first load the fake antivirus set in the registry
C:\Documents and Settings\{username}\Local Settings\Application Data\av.exe” /START “%1″ %*”
Here the malware av.exe is run followed by the actual executable. The malware has been developed to call the real program after its own program has loaded.
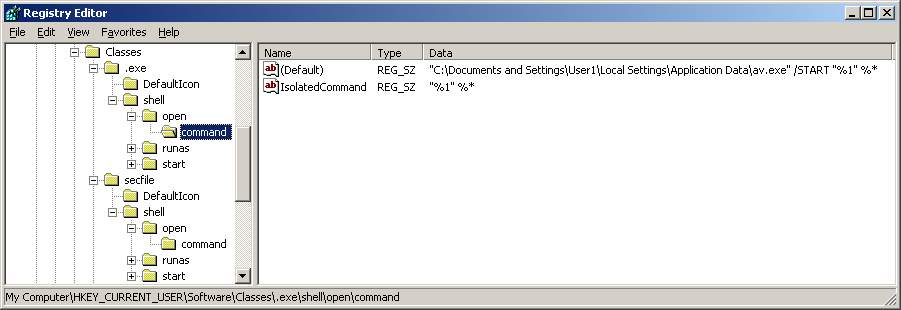
Another interesting entry in the registry made by the malware is when an executable is called Windows checks another location in the registry. This entry is not available in HKEY_CURRENT_USER but even if it was the value would have been exefile and not secfile. So what happens is Windows now checks the .exe key and sees secfile value, this points to the secfile key where is sees Application value which finally points to the exefile key in HKEY_LOCAL_MACHINE.
[HKEY_CURRENT_USER\Software\Classes\.exe]
@=”secfile”
points to . . .
[HKEY_CURRENT_USER\Software\Classes\secfile]
@=”Application”
which points to . . .
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\exefile]
@=”Application”
So in the future if you think your exe association has been hijacked first area to check the .exe key in the registry and go from there. On a Windows XP machine by default HKEY_CURRENT_USER will not have an .exe key and only the values below in the HKEY_LOCAL_MACHINE .exe key.
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\.exe]
@=”exefile”
“Content Type”=”application/x-msdownload”
[HKEY_LOCAL_MACHINE\SOFTWARE\Classes\.exe\PersistentHandler]
@=”{098f2470-bae0-11cd-b579-08002b30bfeb}”
If you want to test exe hijacking you can save the following lines below in reg file and import it. From their on any executable run will load up Windows Calculator. Once testing is finished you can simply delete the .exe key in HKEY_CURRENT_USER. The same applies in the HKEY_LOCAL_MACHINE but here you cannot delete the .exe key. So if you want to test using HKEY_LOCAL_MACHINE I recommend you backup the .exe key first.
Windows Registry Editor Version 5.00
[HKEY_CURRENT_USER\Software\Classes\.exe]
@=”anything”
[HKEY_CURRENT_USER\Software\Classes\.exe\shell]
[HKEY_CURRENT_USER\Software\Classes\.exe\shell\open]
[HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command]
@=”\”C:\\windows\\system32\\calc.exe\””
Reference:
http://www.threatexpert.com/report.aspx?md5=6472e446c64a34edf7fe4ae8270e6faf