Here are some well known anti-rootkit scanners that are a must have in your tools collection. Its always good to have a couple of anti-rootkit scanners as you might find some scanners may not detect all rootkits. The download links are for those versions mentioned in the table at the time of this post so for future versions I recommend you visit the sites to make sure you obtain the latest version.
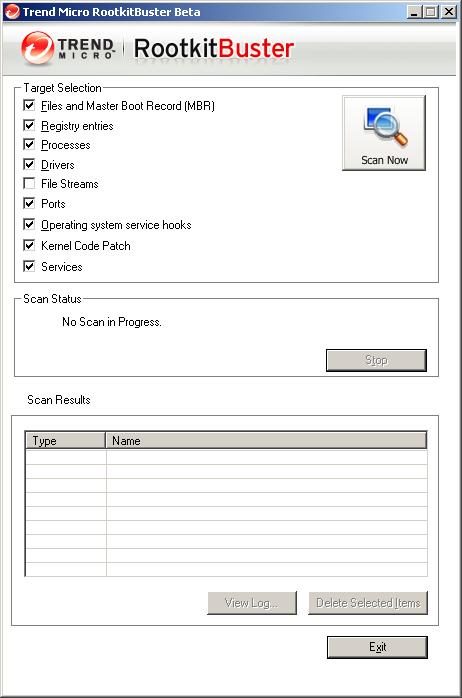
My favourite one is Trend Micro’s RootkitBuster, not just for its performance and design but also because Trend Micro has done a good job in keeping its tool up-to-date with new detection features.