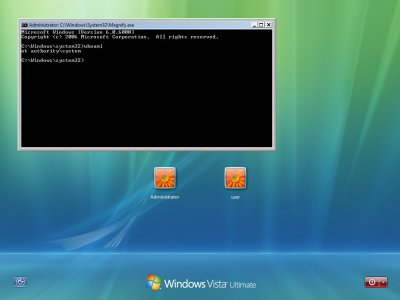
Windows Vista’s backdoor method works by exploiting the “Ease of Access” button at the bottom left of the Windows Vista Logon screen. Normally when the icon is clicked we get a choice of options such as Narrator, Magnifier, etc.
The way to exploit this is by replacing any one of the files with your own executable and calling it the same name. Say if magnify.exe was replaced with cmd.exe then selecting the magnify option would bring up the console window.
Obviously in order to replace such windows files you will first need to logon to the system with admin rights, take ownership of the file and then replace the file with with one of your own.
If you ever forgot your local logon password you could use this backdoor method and reset the password or connect to a remote share and copy your files over.
The choices of files you can modify to get the backdoor working are:
magnify.exe, narrator.exe, osk.exe or utilman.exe
The utilman.exe is the main executable that brings up the Ease of Access window which references the rest of the executables.
If you wanted to capture someone’s logon credentials, normally even with local admin rights to the box, majority key logging tools do not intercept keystrokes at the ctrl+alt+del stage whether the tool has been loaded up at boot as a service or as a program.
This backdoor method works a treat in an office environment for capturing passwords.
1. Remotely connect to a desktop machine
2. Replace a file say utilman.exe with your key logger
3. Walk upto the desk and click on the “ease of access” button
Now just wait for the user to logon to capture the credentials :). Once logged in the key logger terminates.
The Windows function GetAsyncKeyState() is all it takes to design a key logger and is the easiest option.
One solution to mitigate the risk would be to make sure the utilman.exe executable does not get replaced or executed. Various products on the market will be able to lock it down.
Reference:
http://www.computerperformance.co.uk/vista/vista_backdoor_logon.htm