Microsoft Windows operating systems come installed with a Windows Installer engine which is used by MSI packages for installation. One of the powerful features is that MSI packages can be installed with elevated privileges for non-admin users. For a package to use elevated privileges the a registry name “AlwaysInstallElevated” must exist in both keys with a dword value of 1.
[HKEY_CURRENT_USER\Software\Policies\Microsoft\Windows\Installer]
“AlwaysInstallElevated”=dword:00000001
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\Installer]
“AlwaysInstallElevated”=dword:00000001
These settings normally do not exist so must be present to begin with in order to be abused. AD administrators may have enabled these settings allowing users the ability to manually install packages requiring higher privileges while keeping the user rights as non-admin. MSI packages deployed via group policy do not depend on these local registry settings to be present as these packages get deployed with elevated privileges. If manual installation is not required by users then it is safe to change these registry values to 0.
If you do find your corporate pc with these values enabled and do not have local admin rights then it’s just a matter of building your own MSI package and telling it what to do. In the screenshot below I developed a proof of concept tool which shows checking the key values, installing the MSI package which installs a Windows service spawning a local system command shell and finally removing the package.
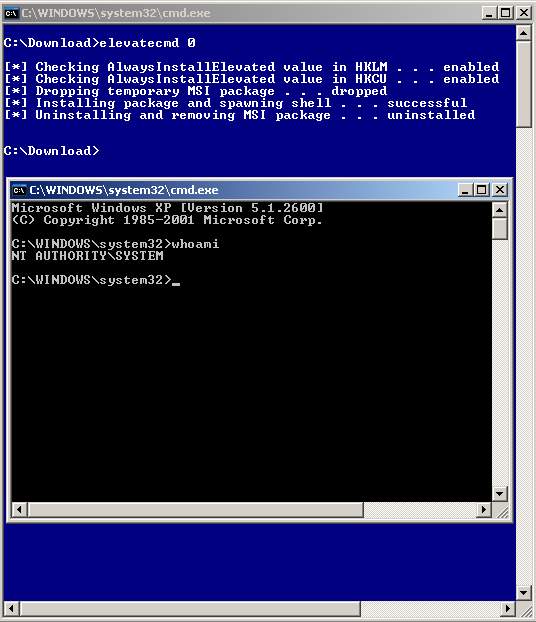
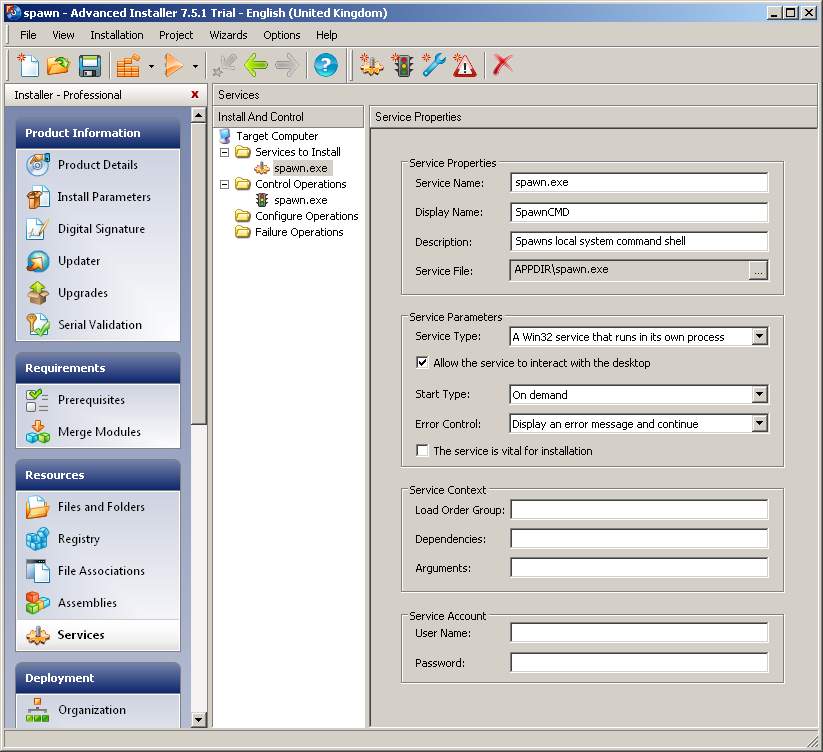
If you are thinking of building an MSI package or any MSI package for that matter I would recommend purchasing “Advanced Installer” by Caphyon. It is a well designed professional software and has all the features you need.
References:
http://www.advancedinstaller.com
http://msdn.microsoft.com/en-us/library/aa367561(VS.85).aspx